Android Tutorial: Use LeakCanary to detect memory leaks - Hallo sahabat Google Android Developer Tutorial, Pada Artikel yang anda baca kali ini dengan judul Android Tutorial: Use LeakCanary to detect memory leaks, kami telah mempersiapkan artikel ini dengan baik untuk anda baca dan ambil informasi didalamnya. mudah-mudahan isi postingan
Artikel android,
Artikel leak,
Artikel memory, yang kami tulis ini dapat anda pahami. baiklah, selamat membaca.
Judul : Android Tutorial: Use LeakCanary to detect memory leaks
link : Android Tutorial: Use LeakCanary to detect memory leaks
In this tutorial we will create a leaked application and we will use the LeakCanary library to detect the memory leak.
Then, the main activity (leaked one), will use the singleton and then we'll go to a new activity:
Then, in the new activity we'll call System.gc to force the garbage collector in order to accelerate the analysis.
The result can be retrieved from logcat:
Complete documentation of LeakCanary can be found in the following links:
https://corner.squareup.com/2015/05/leak-canary.html
https://github.com/square/leakcanary
Anda sekarang membaca artikel Android Tutorial: Use LeakCanary to detect memory leaks dengan alamat link https://googleandroiddevelopertutorial.blogspot.com/2016/01/android-tutorial-use-leakcanary-to.html
Judul : Android Tutorial: Use LeakCanary to detect memory leaks
link : Android Tutorial: Use LeakCanary to detect memory leaks
Android Tutorial: Use LeakCanary to detect memory leaks
Overview
The memory leak can be a headache to detect and to resolve, small memory leaks can be hidden and may be seen after a long usage of the application and hunting memory leaks is not a simple task.In this tutorial we will create a leaked application and we will use the LeakCanary library to detect the memory leak.
Step 1: add the LeakCanary dependency to the application
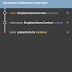
Modify the app/build.gradle to add the LeakCanary dependency as follows:Step 2: Extend and configure the Application class
We need to call LeakCanary.install in onCreate method:Step 3: Create a leaked activity
For this we will create a singleton class that saves the context:Then, the main activity (leaked one), will use the singleton and then we'll go to a new activity:
Then, in the new activity we'll call System.gc to force the garbage collector in order to accelerate the analysis.
Step 4: Retrieve the analysis result
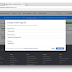
A nice notification can be shown:The result can be retrieved from logcat:
Source code
Complete source code of the sample can be found in Github.Complete documentation of LeakCanary can be found in the following links:
https://corner.squareup.com/2015/05/leak-canary.html
https://github.com/square/leakcanary
Demikianlah Artikel Android Tutorial: Use LeakCanary to detect memory leaks
Sekianlah artikel Android Tutorial: Use LeakCanary to detect memory leaks kali ini, mudah-mudahan bisa memberi manfaat untuk anda semua. baiklah, sampai jumpa di postingan artikel lainnya.
Anda sekarang membaca artikel Android Tutorial: Use LeakCanary to detect memory leaks dengan alamat link https://googleandroiddevelopertutorial.blogspot.com/2016/01/android-tutorial-use-leakcanary-to.html
Android Tutorial: Use LeakCanary to detect memory leaks
4/
5
Oleh
Unknown